
By
- Rahul Awati
What is password salting?
Password salting is a technique to protect passwords stored in databases by adding a string of 32 or more characters and then hashing them. Salting prevents hackers who breach an enterprise environment from reverse-engineering passwords and stealing them from the database.
Password salting increases password complexity, making them unique and secure without affecting user experience. It also helps prevent hash table attacks and slows down brute-force and dictionary attacks.
Password hashing and why salting is required
Hashing prevents passwords from being exposed or stolen by threat actors, since they are not stored as plaintext. For example, when users create an account with a username and password on a website, their password is hashed and stored in an internal file system in an encrypted form.
When users log in, the password runs through a one-way hashing algorithm that converts the password into a different and unrecognizable string of characters. During login, this string is compared to the other hashes stored in the website's database. If the credentials match the stored hash, users can access the account. If it doesn't match, hash verification fails, and users are not able to log in.
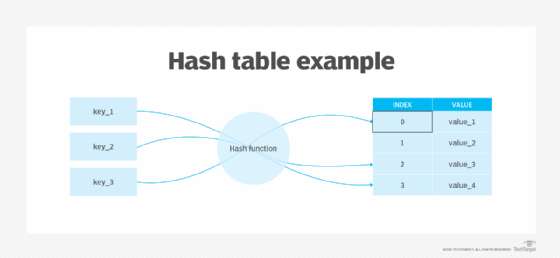
Although hashing is a safe way to store passwords compared to storing them in plaintext, the process is not without problems. One limitation is that, if two passwords are the same -- which is quite common because people tend to use common passwords, like "123456" and "password" -- the hashes generated are also identical.
This makes it easier for a bad actor to crack the passwords by brute-force attacks, dictionary attacks or rainbow attacks and compromise the accounts of multiple users, steal their data or cause other problems. To address this challenge, salting is required.
How password salting works
With password salting, a random piece of data is added to the password before it runs through the hashing algorithm, making it unique and harder to crack.
When using both hashing and salting, even if two users choose the same password, salting adds random characters to each password when the users enter them. As a result, completely different hashes are generated to prevent the passwords and accounts from being compromised.
Here's how it works:
User Password 1 – orange
Salt 1 – y3Unz
Salt added to password 1 – orangey3Unz
Hash ("orange" + salt) 1 - 024ca8e38b33f9116c151123eb432d20
User Password 2 – orange
Salt 2 – 1Hx$
Salt added to password 2 – orange1Hx$
Hash ("orange" + salt) 2 - 5d41402abc4b2a76b9719d911017c592
To prevent password attacks, salts must be unique and random for each login. Encrypting password storage at rest can provide additional Defense in depth, even if a hacker were able to recalculate hashes of common password lists using a given salt for a password.
Which attacks can password salting prevent or minimize?
Attackers use many tools to crack password hashes. This is because hash tables are designed to be fast but are not necessarily secure. By adding randomness to the original plaintext password value before hashing, salting ensures that a different hashed value is generated.
Salting is an additional layer of security to prevent, or at least minimize, the possibility of password compromise by the following three primary attack vectors.
Brute-force attacks
In this type of attack, hackers try to guess every possible password combination and then run these combinations through a hashing algorithm. Once a match is found, they can find the original password. Since password salting creates unique hashes for each password, the attacker cannot guess the original password by brute force.
Dictionary attacks
Dictionary attacks are the advanced version of brute-force attacks. In this type of attack, bad actors try the most common password word and character combinations. They use a prearranged word list with their computed hash and then compare the hashes from a stolen password table with every hash on the list. If they manage to find a match, they can easily find the password. Salting makes this process more difficult and mitigates dictionary attacks.
Rainbow table attacks
Attackers often use rainbow tables to crack unsalted hashes. A rainbow table is a pre-computed database of decrypted hash passwords, which attackers can search to find the desired hash. But, when salting is used for each password, attackers will fail. Even if they know the salt, they would still need to build a rainbow table for each salt. This is how password salting helps prevent rainbow table attacks.

Tips for making the best use of password salting
Here are some ways to make the best use of password salting to strengthen security and prevent password attacks:
- Create a unique salt for every user and password. A unique salt for every user and password increases the computational power required by an attacker to crack passwords. A unique salt should also be generated every time users change their password.
- Store salt and password separately. Storing the salt separately from the password makes it harder for attackers to reverse-engineer the password.
- Make the salt at least the same length as the output hash. The length of the salt value should be long and at least of the same length as the output hash.
- Use a pseudo-random number generator. Using a cryptographically secure pseudo-random number generator to salt the values of hash passwords generates random and unpredictable values that are difficult for attackers to compromise.
- Add a secret key to the hash. This ensures that the password can only be validated if the secret key is known. Storing the key separately on an external system also stops hackers because they need to access both internal and external systems to carry out a password-based attack.
- Don't use usernames as hash values. Usernames are predictable and often reused, leaving the account susceptible to hacking.
- Don't use a systemwide salt. A systemwide salt allows an attacker to use hash tables to steal passwords and compromise accounts. Instead, each password created for a user should be hashed and salted separately.

Explore why security professionals recommend implementing an effective identity and access management system and the role employee training plays in password and cybersecurity strategy. Also, learn about passwordless authentication options and best practices, the difference between a password and a PIN, and how to create good passwords and add security layers.
This was last updated in December 2021
Continue Reading About password salting
- 5 password management tips for MSP customers
- How to ensure security for 3 types of digital identity
- Biometric security technology could see growth in 2021
- For minimum password length, are 14-character passwords sufficient?
- What is a password spraying attack and how does it work?
Related Terms
- crisis management plan (CMP)
- A crisis management plan (CMP) outlines how an organization should respond to a critical situation that if left unaddressed, ...Seecompletedefinition
- firewall as a service (FWaaS)
- Firewall as a service (FWaaS), also known as a cloud firewall, is a service that provides cloud-based network traffic analysis ...Seecompletedefinition
- sandbox
- A sandbox is an isolated testing environment that enables users to run programs or open files without affecting the application, ...Seecompletedefinition
Dig Deeper on Application and platform security
- China claims it cracked Apple's AirDrop, can track sendersBy: AlexanderCulafi
- single-factor authentication (SFA)By: TechTargetContributor
- rainbow tableBy: AlexanderGillis
- Are 14-character minimum-length passwords secure enough?By: SharonShea